SNA #3: Understanding VXLAN
Todays topic:
Quick definition of vxlan
VXLAN stands for Virtual Extensible LAN, it’s a new approach to network virtualization, designed for large cloud computing deployments to meet their challenges of scaling. At its most basic level, VXLAN is a tunnelling protocol. It’s an encapsulation technique in which layer 2 ethernet frames are encapsulated in UDP packets. In OSI model it represents another application layer-protocol based on UDP that runs on port 4789. But why has VXLAN captured the attention of the networking community?
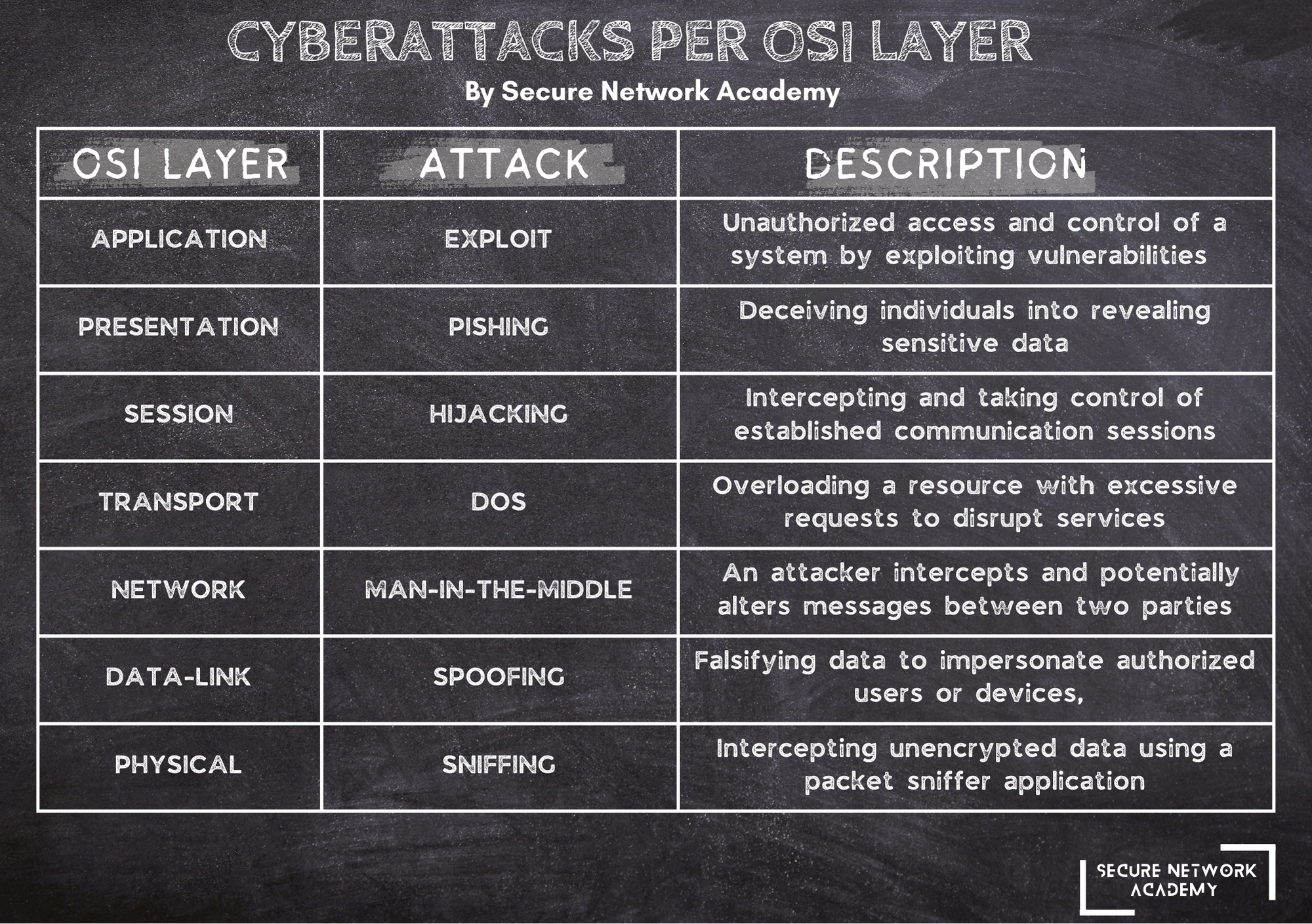
Application Layer: Exploit
At the uppermost layer of the OSI model, the Application Layer, we encounter a variety of software vulnerabilities. Attackers often exploit these weaknesses to gain unauthorized access and seize control of systems. These exploits may also enable diverse types of attacks, including the notorious denial-of-service (DoS) attacks.
Presentation Layer: Phishing Attacks
Moving down to the Presentation Layer, phishing attacks take center stage. Phishing is a pervasive cyber threat that deceives individuals into revealing sensitive data through an assortment of tactics. This type of attack has evolved into a multifaceted menace, encompassing various subtypes.
Session Layer: Hijacking Attacks
The Session Layer introduces hijacking attacks, where malicious actors intercept and wrest control of an established communication session. The goal here can be twofold: either to access sensitive data or to gain unauthorized entry into a user's computer or account.
Transport Layer: Reconnaissance and DoS Attacks
Beneath that, at the Transport Layer, we encounter reconnaissance attacks. While initially conceived as an ethical hacking technique to identify security gaps, it has also become a prelude to cyberattacks. Simultaneously, Denial-of-Service (DoS) attacks emerge, where attackers flood a resource with excessive requests, causing temporary or indefinite disruption. Distributed versions of this attack are known as DDoS attacks.
Network Layer: Man-in-the-Middle Attacks
As we delve into the Network Layer, we confront the ominous Man-in-the-Middle (MitM) attacks. In MitM attacks, an assailant cunningly positions themselves between two communicating parties. This allows them to clandestinely monitor, relay, and even manipulate message content, all while both parties believe they're communicating securely.
Data Link Layer: Spoofing Attacks
Descending further to the Data Link Layer, spoofing attacks come into play. These attacks involve the falsification of data to appear as an authorized user or device. By impersonating legitimate entities, attackers can sidestep access controls, pilfer data, and proliferate malware.
Physical Layer: Sniffing Attacks
Finally, at the Physical Layer, we confront sniffing attacks. These attacks entail the interception of unencrypted data using packet sniffer applications. The captured data can then be analyzed, potentially leading to network disruption or even crashes.